Below is an overview of how many organizations are now approaching “modern SOC” (Security Operations Center) architecture and deployment. The goal is to build something that is efficient, scalable, secure, and that lets humans focus on higher-value tasks by leveraging automation, AI/ML, and cloud infrastructure. While specific vendor or open-source selections differ from one environment to another, the overall architectural pillars and best practices tend to be consistent.
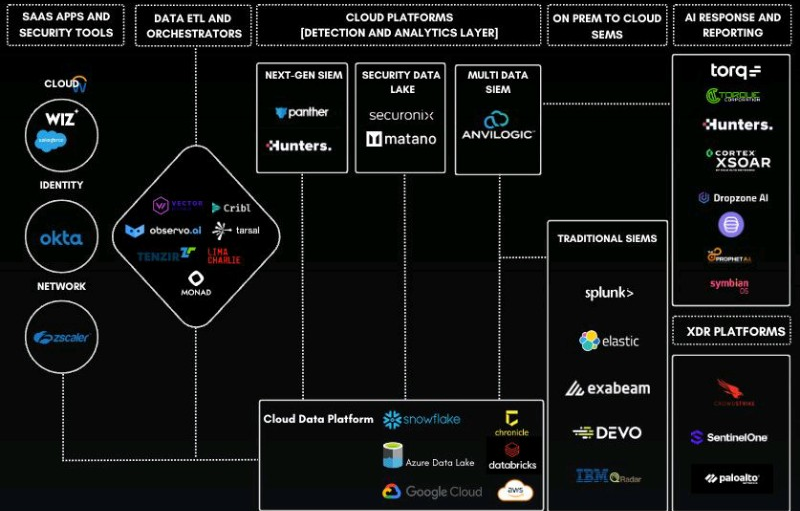
1. Ingestion and Integration of Logs/Events
- SaaS and Cloud-Native Services
Organizations often use multiple security tools (e.g., cloud posture management like Wiz or Lacework, identity services like Okta, and network security services like Zscaler) that each generate large volumes of data. - Data ETL and Orchestrators
Tools such as Cribl, Tenzir, or ObservIQ help aggregate and transform these disparate logs into standardized formats before they land in a data lake or SIEM. This reduces duplication, controls log volume, and enriches data (e.g., adding geolocation, threat intel context).
Key Benefit: By funneling all relevant data through a consistent ETL/orchestration layer, the SOC team eliminates the “blind spots” that come from scattered event collection and gets a uniform view for downstream analysis.
2. Centralized Data Lake and SIEM
- Security Data Lake
Traditionally, SOC teams have used on-prem SIEMs as both the ingestion pipeline and the database of record. Now, “cloud data lake” approaches allow for more flexible retention, cheaper storage, and near real-time analytics with platforms like Snowflake, Databricks, BigQuery, or Amazon S3-based data lakes. - Next-Generation SIEM
Solutions like Panther, Hunters, or Anvilogic often act as a detection analytics layer on top of your data lake. They provide dynamic correlation, machine learning-based threat detection, and more advanced analytics than many legacy SIEMs could offer.
Key Benefit: Decoupling the data lake (where raw logs live) from the SIEM or analytics platform (which queries and correlates events) creates better scalability—your detection platform can query exactly what it needs, when it needs it.
3. Detection and Analytics Layer
- AI/ML for Threat Detection
Modern SOC deployments often incorporate machine learning or anomaly detection modules (e.g., advanced user and entity behavior analytics—UEBA). This is sometimes built into newer SIEMs or XDR solutions. - Threat Intelligence Integration
Most modern platforms integrate threat intelligence feeds (either commercial or open-source) in real time, automatically tagging relevant logs or correlating known bad IPs, domains, or file hashes.
Key Benefit: AI/ML-based detections help handle “heavy lifting” around looking for subtle anomalies or suspicious behaviors in massive data sets, freeing analysts to investigate the high-fidelity alerts rather than manually triaging thousands of daily events.
4. On-Prem to Cloud SIEM Migration
- Hybrid Environments
Many organizations are still running some security tooling and SIEM components on-premises (e.g., Splunk, IBM QRadar, Elastic). Modern SOC designs often move the analysis layer to the cloud, while data ingestion can remain partly on-prem. - Incremental Migration
A staged approach can let organizations slowly offload storage and analytics to cloud services, easing migration pains and cost concerns.
Key Benefit: You get the best of both worlds—continued use of existing on-prem solutions and log collection, combined with the scale and flexible pricing of cloud-based data lakes and analytics layers.
5. Automated Response and SOAR
- Security Orchestration, Automation, & Response (SOAR)
Platforms like Palo Alto Cortex XSOAR, Torq, or Tines automate common response playbooks—blocking IP addresses, isolating machines, opening tickets, or sending notifications. - AI-Driven Investigations
Some platforms now offer AI-based triage capabilities (e.g., summarizing relevant alerts, automatically gathering endpoint data, or mapping to MITRE ATT&CK). This reduces manual cycles so analysts can focus on deeper investigations.
Key Benefit: Orchestrated, automated response is crucial to a modern SOC. It handles routine tasks (e.g., collecting logs, quarantining compromised hosts), letting humans focus on complex analysis and strategic improvements.
6. XDR and Consolidated Endpoint/Cloud Visibility
- Extended Detection and Response (XDR)
Vendors like CrowdStrike, SentinelOne, or Microsoft Defender for Endpoint unify endpoint telemetry with broader identity, email, and cloud data to provide “extended” detection coverage. - Single Pane of Glass
By consolidating endpoint, network, and cloud telemetry into one detection plane, XDR tools reduce alert noise and speed up triage.
Key Benefit: XDR offers an integrated approach for threat detection across endpoints and servers, often using a single agent for advanced logging, threat prevention, and real-time response.
7. People and Processes in the Modern SOC
Despite the wealth of automation and AI, the human element remains critical. Modern SOC workflows incorporate:
- Tiered Analyst Structure
- Tier 1 focuses on alert triage and initial investigation.
- Tier 2 hunts for threats, tunes detection rules, and works on complex incidents.
- Tier 3 (or Engineering) maintains the platform, fine-tunes detection logic, and integrates new sources.
- Automation of Routine Tasks
- Use orchestration to handle mundane actions: IP blocks, user notifications, ticket generation.
- Automate threat hunting queries on a schedule and only escalate anomalies.
- Continuous Optimization
- Detection as Code: Manage detection rules, correlation searches, and playbooks in version-controlled repositories.
- Proactive Threat Hunting: Regularly test detection coverage with red/purple team exercises.
Key Benefit: Well-defined processes, with humans focusing on creative, strategic, or complex investigations, ensure the SOC can scale without burning out analysts on repetitive tasks.
8. Putting It All Together: Efficiency, Scale, Security
- Ingest Everything Once, at Scale
- Centralize logs and telemetry via an ETL layer that can scale horizontally.
- Store data in a cloud data lake for cost-effective retention and flexible querying.
- Apply Real-Time (and Retroactive) Analytics
- Next-gen SIEM or XDR layers continuously monitor new events, auto-enrich with threat intel, and apply ML-based detections.
- Retrospective queries let analysts pivot quickly over days or months of data when investigating advanced threats.
- Automate Response Workflows
- SOAR platforms unify investigation steps, escalate critical alerts to human analysts, and handle routine tasks automatically.
- Ensure Visibility Across Hybrid Environments
- Extend monitoring to SaaS, multi-cloud, containers, on-prem servers, and network edge.
- Leverage AI to “Do the Heavy Lifting”
- Use anomaly detection, correlation engines, and AI-based triage for large data volumes.
- Free human analysts to focus on higher-level threat hunting, incident response, and strategy.
Conclusion
A modern SOC that is efficient, scalable, and secure rests on the foundation of unified data ingestion, cloud-scaled storage and analytics, AI/ML-driven detection, and automated response. While no single tool covers every aspect perfectly, building the SOC as an open ecosystem—where data can flow between best-in-class solutions—offers the greatest flexibility.
Most importantly, the human element must be empowered with reliable, high-fidelity alerts, user-friendly investigative workflows, and efficient automation so they can spend time on the true threats rather than drowning in mundane tasks. By designing a SOC architecture that leverages automation and AI, you position security teams to adapt quickly, reduce response times, and continually refine their threat detection and response capabilities.
