Below is a comprehensive, in-depth article on 20 Key Performance Indicators (KPIs) that CISOs (Chief Information Security Officers) often track. These metrics provide insight into an organization’s security posture, help prioritize resources, and measure the effectiveness of cybersecurity strategies. You can adapt this content for your CISO-centric website or blog.
Introduction
As digital threats grow more sophisticated, CISOs need concrete, data-driven ways to measure how well their security program is performing. Key Performance Indicators (KPIs) play a critical role by providing quantifiable metrics that align security objectives with broader business goals. By tracking these KPIs, CISOs can:
- Demonstrate the value of security investments to executive leadership.
- Identify gaps and weak spots that need immediate attention.
- Benchmark against industry standards and regulatory requirements.
- Foster a security-first culture across the organization.
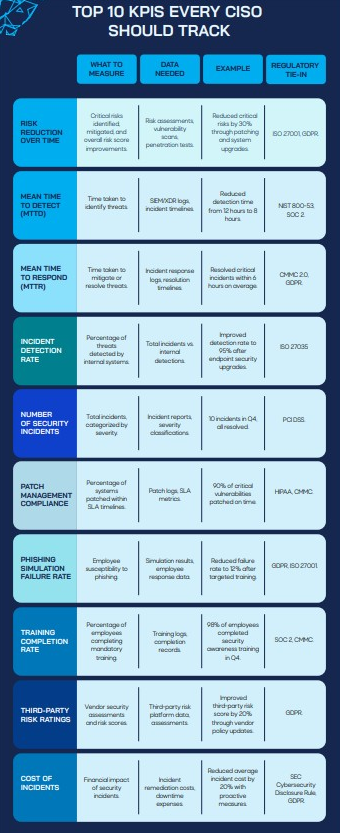
Below are 20 essential KPIs—divided into two sets of 10—spanning foundational metrics such as risk reduction, incident detection, and patch compliance, as well as broader indicators like budget allocation and configuration compliance.
- Risk Reduction Over Time
- Mean Time to Detect (MTTD)
- Mean Time to Respond (MTTR)
- Incident Detection Rate
- Number of Security Incidents
- Patch Management Compliance
- Phishing Simulation Failure Rate
- Training Completion Rate
- Third-Party Risk Ratings
- Cost of Incidents
- Security Configuration Compliance Rate
- Privileged Access Management (PAM) Metrics
- Endpoint Protection Coverage
- Secure Software Development Lifecycle (SSDLC) Metrics
- Mean Time Between Failures (MTBF) for Security Controls
- Backup and Recovery KPIs
- Security Awareness Survey Scores
- Security Spend vs. Organizational Budget
- Data Loss Prevention (DLP) Incident Metrics
- Penetration Test / Red Team Findings Closure Rate
1. Risk Reduction Over Time
-
Definition
Measures how effectively the organization is reducing critical cyber risks, typically by comparing the number of identified risks over a period (monthly, quarterly, yearly) against the number resolved or accepted. -
Data Needed
- Risk assessment results
- Vulnerability scans
- Threat intelligence reports
- Risk acceptance documentation
-
Importance
Shows clear evidence of how the security team is mitigating the most impactful threats. It informs budget decisions, remediation prioritization, and risk acceptance thresholds. -
Regulatory/Framework Tie-In:
- ISO 27001 – risk management processes
- GDPR – data protection impact assessments (DPIA)
2. Mean Time to Detect (MTTD)
-
Definition
The average time from the occurrence of a security event or breach to the point at which the security team becomes aware of it. Also known as “Time to Identify.” -
Data Needed
- Security Information and Event Management (SIEM) data
- Endpoint Detection & Response (EDR) alerts
- Forensic logs
-
Importance
Faster detection can significantly reduce the damage inflicted by malicious actors. A short MTTD often correlates with robust monitoring tools and processes. -
Regulatory/Framework Tie-In:
- NIST 800-53 – continuous monitoring controls
- SOC 2 – security principle requiring timely detection
3. Mean Time to Respond (MTTR)
-
Definition
The average time from the moment a security incident is detected to when it is fully resolved or contained. -
Data Needed
- Incident response plan timelines
- Logs from remediation steps
- Post-incident reviews
-
Importance
Even if detection is swift, a slow response allows the threat to spread. MTTR reflects the maturity and readiness of your incident response team, tools, and processes. -
Regulatory/Framework Tie-In:
- CMMC 2.0 – incident response maturity
- GDPR – 72-hour breach notification requirement
4. Incident Detection Rate
-
Definition
The percentage of actual threats identified by your security systems out of the total known attempted attacks. This includes how effectively your Intrusion Detection Systems (IDS), SIEM, and other controls filter out malicious activity. -
Data Needed
- Total security alerts
- Number of confirmed threats vs. false positives
- Forensic and threat intelligence correlating actual attacks
-
Importance
A high detection rate reflects effective threat intelligence, properly tuned security systems, and vigilant SOC (Security Operations Center) analysts. -
Regulatory/Framework Tie-In:
- ISO 27035 – incident management best practices
5. Number of Security Incidents
-
Definition
A count of total security incidents in a specific timeframe, often broken down by severity (low, medium, high) or type (malware, phishing, insider threats, etc.). -
Data Needed
- Incident logs
- SOC reports
- Severity classification (e.g., critical, high, medium, low)
-
Importance
Offers a top-level snapshot of how frequently your organization experiences attempted or successful attacks. Monitoring trends helps in resource planning and determining if new threats are emerging. -
Regulatory/Framework Tie-In:
- PCI-DSS – incident management for payment card data
6. Patch Management Compliance
-
Definition
The percentage of systems and software patched within the timeframe stipulated by internal SLAs or regulatory standards. -
Data Needed
- Patch management tool logs
- Vulnerability scan outputs
- SLA or policy guidelines on patch timelines
-
Importance
Unpatched vulnerabilities are a leading entry point for attackers. High compliance indicates a proactive approach to reducing known exploits. -
Regulatory/Framework Tie-In:
- HIPAA – timely patching of systems handling electronic Protected Health Information
- CMMC – secure configurations and timely updates
7. Phishing Simulation Failure Rate
-
Definition
The percentage of employees who fall for simulated phishing campaigns—e.g., clicking on suspicious links or providing credentials. -
Data Needed
- Simulation platforms (click rates, form submissions)
- Training records
- Remediation/awareness follow-up data
-
Importance
Humans remain one of the biggest vulnerability points. Reducing the failure rate is critical to improving overall cybersecurity posture. -
Regulatory/Framework Tie-In:
- GDPR and ISO 27001 – emphasize training and awareness
8. Training Completion Rate
-
Definition
The percentage of employees who complete mandatory security awareness training within a designated period (e.g., annual or quarterly). -
Data Needed
- Learning Management System (LMS) records
- Employee training schedule compliance
-
Importance
Reflects how seriously the organization takes security culture. High compliance typically correlates with lower phishing susceptibility and better incident reporting. -
Regulatory/Framework Tie-In:
- SOC 2 – documentation of security training
- CMMC – workforce cybersecurity awareness requirements
9. Third-Party Risk Ratings
-
Definition
A measure of the security posture of vendors, partners, or service providers. Often derived from questionnaires, on-site assessments, or external rating services. -
Data Needed
- Vendor security questionnaires
- Third-party risk platform data
- Contractual requirements & compliance documents
-
Importance
Supply chain attacks are increasingly common. Monitoring third-party risk helps ensure your partners’ vulnerabilities don’t become your own. -
Regulatory/Framework Tie-In:
- GDPR – requiring evaluation of data processors’ security controls
- ISO 27001 – Annex A includes supplier relationships
10. Cost of Incidents
-
Definition
The financial impact of security breaches, covering direct costs (forensic investigations, legal fees, downtime, resource reallocation) and indirect costs (brand damage, lost opportunities). -
Data Needed
- Incident response invoices
- Forensic investigation costs
- Insurance claims and regulatory fines
- Brand impact assessments
-
Importance
Demonstrates the tangible business impact of cybersecurity events, making it easier to justify budgets for tools, training, and personnel. -
Regulatory/Framework Tie-In:
- SEC Cybersecurity Disclosure (for publicly traded companies)
- GDPR (significant financial penalties for non-compliance)
Additional KPIs to Consider
The following 10 KPIs build on the initial list, offering deeper insights into security controls, configurations, budget allocations, and more specialized areas of cybersecurity governance.
11. Security Configuration Compliance Rate
-
Definition
The percentage of systems (servers, endpoints, cloud instances, network devices) that adhere to approved security baselines or recognized benchmarks (e.g., CIS Benchmarks). -
Data Needed
- Configuration management database (CMDB) outputs
- Automated configuration scanning results
- Change management logs
-
Importance
Misconfiguration remains a top cause of data breaches and service outages. Tracking compliance ensures consistency and reduces potential attack surfaces.
12. Privileged Access Management (PAM) Metrics
-
Definition
Monitors the control of privileged accounts, covering:- Number of privileged accounts vs. overall accounts
- Frequency of privileged session activity
- Percentage of privileged sessions audited or recorded
-
Data Needed
- PAM solution logs
- Directory services data (Active Directory, LDAP)
- Access approval workflows
-
Importance
Privileged accounts have elevated rights; if compromised, attackers can inflict serious damage. Proper governance here significantly reduces insider and external threat vectors.
13. Endpoint Protection Coverage
-
Definition
The percentage of endpoints (workstations, servers, mobile devices) with up-to-date antivirus, anti-malware, or EDR software installed and active. -
Data Needed
- Endpoint security tool reports
- Asset inventory
- Patch/update compliance data
-
Importance
Ensures visibility and basic defenses across the entire organization. Gaps in coverage are prime targets for attackers.
14. Secure Software Development Lifecycle (SSDLC) Metrics
-
Definition
Focuses on the maturity of security within the software development process. Common measures include:- Number/percentage of code vulnerabilities discovered in early vs. late stages
- Time to remediate critical findings
- Coverage of automated security tests (SAST, DAST, SCA)
-
Data Needed
- Application security testing logs
- CI/CD pipeline data
- Code review findings
-
Importance
Identifies vulnerabilities early (where they’re cheaper and easier to fix). Reduces the likelihood of pushing insecure code to production.
15. Mean Time Between Failures (MTBF) for Security Controls
-
Definition
Tracks how frequently critical security controls fail or malfunction. For example, a SIEM outage or a malfunctioning firewall rule set. -
Data Needed
- System uptime and downtime logs
- Incident logs detailing root causes
- Monitoring tool alerts
-
Importance
Ensures reliability of essential security infrastructure. Frequent failures can lead to unmonitored windows that attackers can exploit.
16. Backup and Recovery KPIs
-
Definition
Several metrics can be tracked here:- Recovery Point Objective (RPO): The maximum acceptable amount of data loss (e.g., 24 hours).
- Recovery Time Objective (RTO): The target time for restoring operations after an incident.
- Percentage of successful backup verifications/tests.
-
Data Needed
- Backup solution logs
- Disaster recovery test results
- Business impact analysis (BIA) metrics
-
Importance
Demonstrates the organization’s ability to recover from incidents like ransomware or system failures, crucial for business continuity.
17. Security Awareness Survey Scores
-
Definition
Measures employee attitudes and knowledge regarding security through periodic surveys—beyond the pass/fail rates of phishing tests. -
Data Needed
- Anonymous survey responses
- Focus group feedback
- Knowledge quiz results
-
Importance
Gauges the depth of a “security-first” culture. If employees understand policies and can articulate best practices, they are less likely to make critical errors.
18. Security Spend vs. Organizational Budget
-
Definition
The ratio or percentage of the overall IT (or total) budget allocated to cybersecurity. Also tracks how investments shift over time in response to new threats or business objectives. -
Data Needed
- Financial documents (CAPEX, OPEX)
- Security technology and service invoices
- Budget planning data
-
Importance
Illustrates whether the organization is aligning funding with risk appetite and threat landscape. A too-low spend could signal underinvestment; too-high spend might suggest inefficiencies.
19. Data Loss Prevention (DLP) Incident Metrics
-
Definition
Monitors attempts to exfiltrate sensitive data (e.g., intellectual property, personal information) and the effectiveness of DLP solutions in blocking or flagging these attempts. -
Data Needed
- DLP tool logs (email, endpoint, cloud)
- Incident investigations
- Classification labeling data
-
Importance
Data exfiltration is a top concern for regulated industries and IP-centric organizations. Tracking blocked vs. successful attempts reveals insider or external threats targeting sensitive assets.
20. Penetration Test / Red Team Findings Closure Rate
-
Definition
Tracks how quickly and effectively organizations remediate vulnerabilities found during penetration tests, red team exercises, or bug bounty programs. -
Data Needed
- Penetration test reports
- Red team exercise logs and recommended actions
- Vulnerability management platform data
-
Importance
Demonstrates the organization’s responsiveness to known security gaps. A quick closure rate indicates a strong, agile vulnerability management process.
How to Implement and Track These KPIs
- Prioritize by Risk
Not all KPIs carry the same weight. Focus first on those that address your biggest risks or compliance mandates. - Automate Data Collection
Use SIEM solutions, GRC platforms, endpoint management systems, and other tools to gather data in real-time or near-real-time. - Set Baselines and Targets
Determine current performance to establish baselines, then set realistic goals (e.g., reduce phishing failure rate by 50% in one year). - Communicate Regularly
Tailor KPI dashboards for different audiences:
- Executive Leadership – high-level, business-impact metrics like cost of incidents or risk reduction.
- Technical Teams – detailed operational metrics such as MTTD, MTTR, or SSDLC findings.
- Review and Refine
As threats evolve or business objectives change, periodically reassess which KPIs are still relevant and which ones should be introduced or retired.
🎧 Related Podcast Episode
Conclusion
A robust set of KPIs offers a 360° view of your organization’s cybersecurity posture. By combining foundational metrics like Mean Time to Detect and Patch Management Compliance with additional insights such as PAM Metrics and SSDLC measures, CISOs can make data-driven decisions and demonstrate the tangible value of security initiatives to stakeholders at all levels.
Whether you’re just beginning to formalize a security metrics program or looking to deepen an existing framework, these 20 KPIs provide a solid foundation to guide strategic investments, improve operational resilience, and strengthen overall cyber defense.
